Configuration
Configuration takes places in configuration files or can be applied directly in Pimcore backend userinterface.
Configuration Options
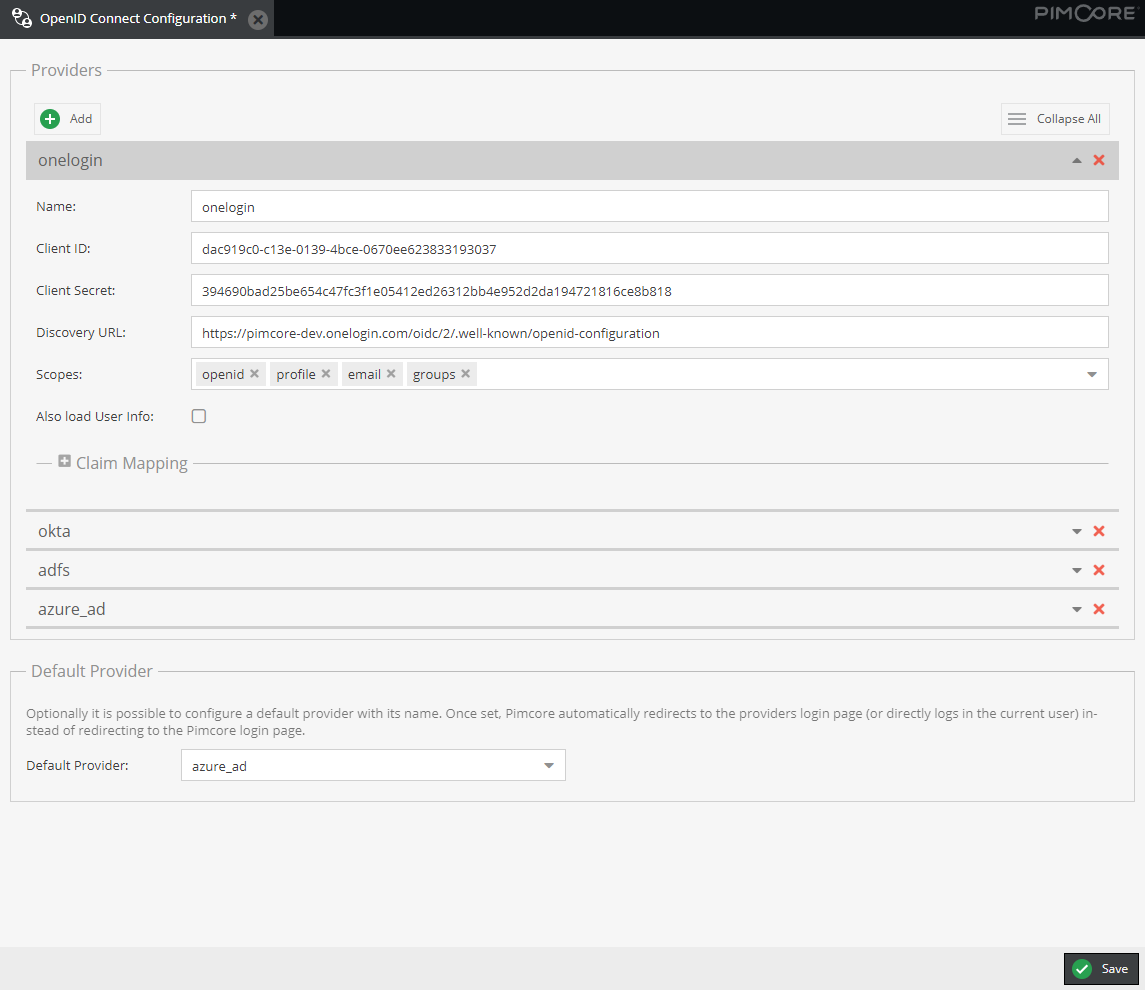
Providers
It is possible to configure multiple OpenID Connect providers in parallel. For each provider and separate login button will be displayed on Pimcore login page. This login button redirects to OpenID Connect provider and starts the OpenID flow.
Each provider has to have a unique name.
On provider side, you normally need to configure an application to allow Pimcore to access. Following informations you might need from Pimocore for that:
- Redirect URL:
https://<YOUR_PIMCORE_DOMAIN>/oidc/endpoint - Allowed scopes:
openid profile groups email(see also settings below)
Following configuration values are necessary per provider on Pimcore side and be available as soon as the application on provider side is setup:
client_id: Client ID provided by the provider.client_secret: Client secret provided by the provider.url_discovery: Endpoint for openid configuration discovery, based on https://openid.net/specs/openid-connect-discovery-1_0.html. Typically it is something like<PROVIDER_DOMAIN>/.well-known/openid-configuration.
Optionally, following additional options can be provided for each provider:
scopes: Customize the scopes for the OpenId Connect flow. By default,openid,profile,emailandgroupsis set as scope.openidwill always be added automatically, as it is required for any OpenId Connect flow.load_user_info: Sometimes it is necessary to also call the user info endpoint of the provider to get all the necessary information about the user as theid-tokendoes not contain it. Setting this setting totruewill initiate this additional call. If not necessary, it should be prevented, as it slows down the sign-on process.claim_mapping: Some provides do not apply to claim names of the OpenId Connect standard. With this setting you can configure custom names for the supported claimspreferred_username(contains the username),given_name,family_name,email,groups(should contain an array of groups the user is assigned to),picture(URL to fetch the user avatar) andsub(remote-id of the user).
Default Provider
Optionally it is possible to configure a default provider with its name. Once set, Pimcore automatically redirects to the providers login page (or directly logs in the current user) instead of redirecting to the Pimcore login page.
If default provider is set, it is still possible to open Pimcore login page when entering its url
(https://<YOUR_DOMAIN>/admin/login) directly to login with local user accounts.
Configuration Storage
The configuration user interface utilizes the LocationAwareConfigRepository for storing the configuration. In the symfony tree the
storage location can be configured, possible values are
symfony-config- write configs as Symfony Config as YAML files to/var/config/oidc/pimcore_open_id_connect.yamlsettings-store- write configs to the SettingsStoredisabled- do not allow to edit/write configs at all
Details also see Pimcore Docs.
Example
pimcore_open_id_connect:
config_location:
open_id_connect:
write_target:
type: 'symfony-config'
options:
directory: '/var/www/html/var/config/oidc'
Additionally, it is also possible to define the configuration directly in a symfony configuration file without using the configuration user interface. In this case, the configuration user interface is just read only.
Sample Configuration File
pimcore_open_id_connect:
default_provider: onelogin
providers:
onelogin:
client_id: <CLIENT_ID>
client_secret: <CLIENT_SECRET>
url_discovery: https://<USERNAME>.onelogin.com/oidc/2/.well-known/openid-configuration
okta:
client_id: <CLIENT_ID>
client_secret: <CLIENT_SECRET>
url_discovery: https://<USERNAME>.okta.com/.well-known/openid-configuration
load_user_info: true
scopes:
- profile
- email
- groups
claim_mapping:
preferred_username: preferred_username
given_name: given_name
family_name: family_name
email: email
groups: groups
picture: picture
sub: sub
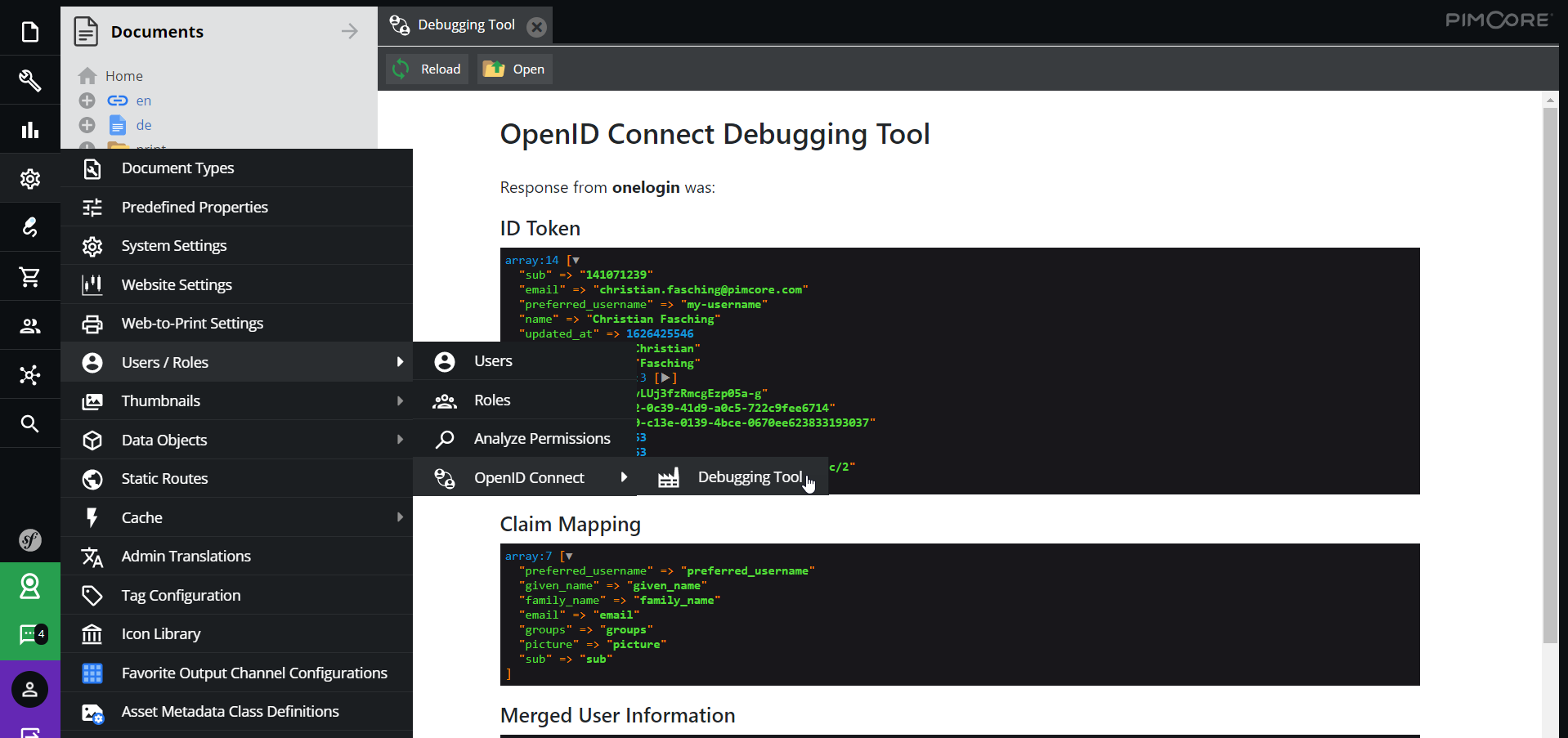
Debugging
The bundle provides a debug window for setting up the OpenId Connect integrations. It is located in the settings menu of the toolbar in the users sub menu. The debug window lists all the configured providers, allows to send test sign-on requests and see the response of the providers in order to setup the claim mappings properly.